Exploring the Power of Nmap NSE Scripts: Expanding Network Scanning Capabilities
Related Articles: Exploring the Power of Nmap NSE Scripts: Expanding Network Scanning Capabilities
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Exploring the Power of Nmap NSE Scripts: Expanding Network Scanning Capabilities. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Exploring the Power of Nmap NSE Scripts: Expanding Network Scanning Capabilities
- 2 Introduction
- 3 Exploring the Power of Nmap NSE Scripts: Expanding Network Scanning Capabilities
- 3.1 The Essence of NSE Scripts: Beyond Basic Scanning
- 3.2 Unleashing the Power of NSE Scripts: A Comprehensive Overview
- 3.3 Demystifying Nmap NSE Scripts: A Guide to Implementation
- 3.4 Frequently Asked Questions: Navigating the NSE Script Landscape
- 3.5 Tips for Effective Utilization: Maximizing NSE Script Benefits
- 3.6 Conclusion: Embracing the Power of NSE Scripts
- 4 Closure
Exploring the Power of Nmap NSE Scripts: Expanding Network Scanning Capabilities

Nmap, the ubiquitous network scanner, offers a robust suite of tools for network exploration and security assessment. While its core functionality provides valuable insights into network topology and open ports, its true power lies in its extensibility through the use of Nmap Scripting Engine (NSE). NSE scripts, written in Lua, enable users to perform specialized scans, gather detailed information, and automate complex tasks, significantly enhancing Nmap’s capabilities.
The Essence of NSE Scripts: Beyond Basic Scanning
NSE scripts, often referred to as Nmap scripts, are small programs that extend Nmap’s functionality by performing various actions beyond traditional port scanning. These scripts can be categorized into different types, each tailored to specific purposes:
-
Discovery Scripts: These scripts identify network devices, services, and vulnerabilities by leveraging specific protocols or characteristics. For example, the
bannerscript extracts banner information from services, providing valuable clues about the underlying software and version. -
Vulnerability Detection Scripts: These scripts actively test for known vulnerabilities, providing crucial information for security assessments. The
http-vuln-cve2014-3566script checks for the Heartbleed vulnerability, for instance. -
Service Enumeration Scripts: These scripts gather detailed information about specific services, aiding in understanding their configuration and potential weaknesses. The
mysql-infoscript, for example, retrieves information about MySQL databases and users. -
Network Information Gathering Scripts: These scripts collect comprehensive information about network devices, such as operating system details, MAC addresses, and device types. The
smb-osscript, for example, attempts to identify the operating system of a device based on its SMB responses.
Unleashing the Power of NSE Scripts: A Comprehensive Overview
The benefits of utilizing NSE scripts in Nmap are multifaceted:
1. Enhanced Information Gathering: NSE scripts provide a deeper understanding of network devices and services by collecting detailed information beyond basic port scanning. This information can be crucial for security assessments, network management, and incident response.
2. Automated Vulnerability Detection: NSE scripts automate the process of identifying known vulnerabilities, saving time and effort compared to manual testing. This enables security professionals to quickly identify and address potential risks.
3. Targeted Scanning: NSE scripts allow for highly targeted scans by focusing on specific services, protocols, or vulnerabilities. This ensures that the scan is efficient and relevant to the user’s needs.
4. Scripting Customization: The ability to write custom NSE scripts empowers users to tailor Nmap’s capabilities to their specific requirements. This allows for the development of unique scripts that address specific needs and workflows.
5. Community-Driven Development: Nmap’s extensive community of users and developers contributes to a vast library of NSE scripts, providing a wealth of readily available tools for various tasks. This ensures that users have access to a wide range of scripts for their specific needs.
Demystifying Nmap NSE Scripts: A Guide to Implementation
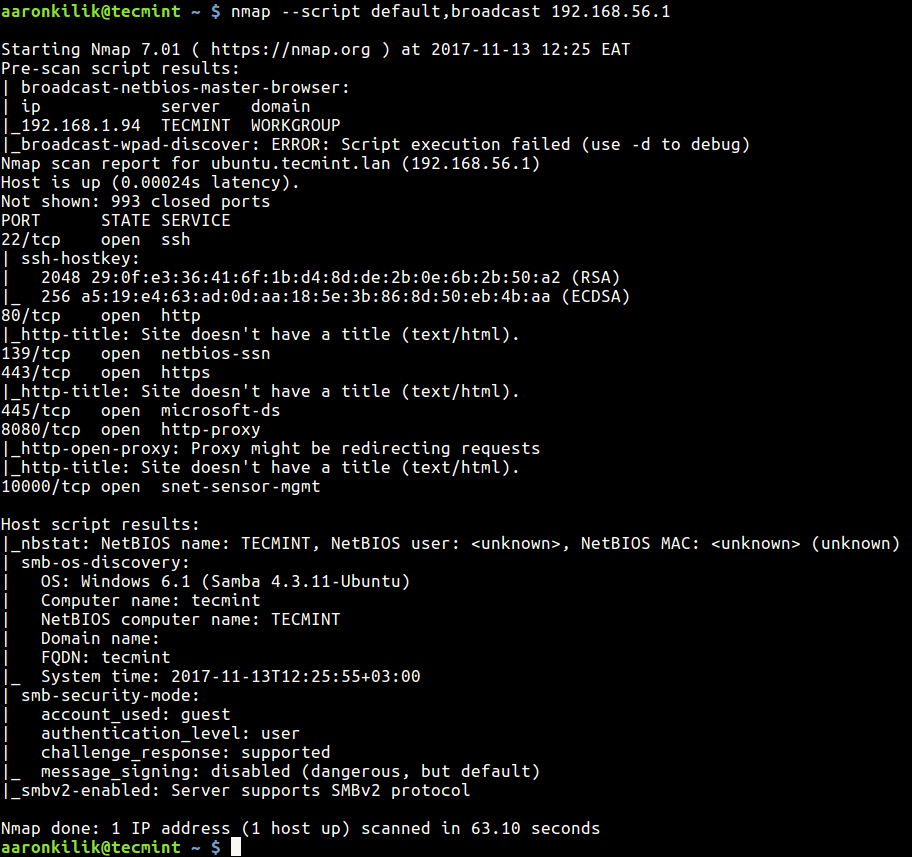
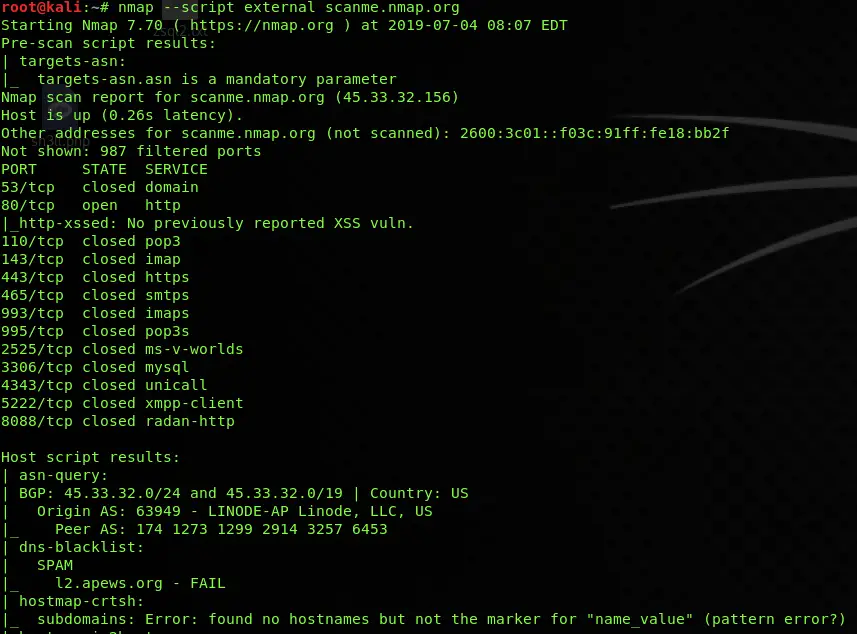
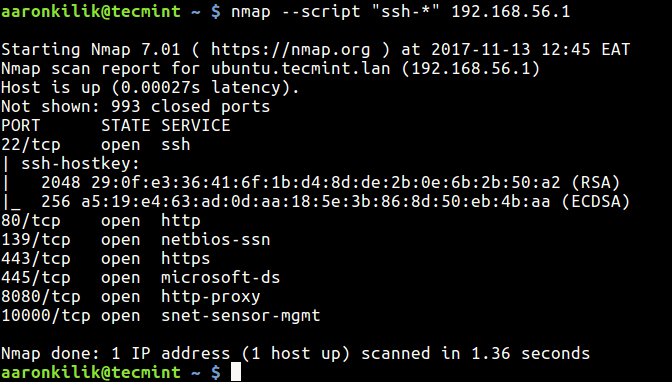
Utilizing NSE scripts in Nmap is straightforward. The -sC option enables the execution of default scripts, while the -sT option allows for the execution of specific scripts. Additionally, users can specify the desired scripts using the --script option, providing granular control over the scanning process.
Example 1: Executing Default Scripts:
nmap -sC -p 80,443 target.comThis command performs a scan against target.com on ports 80 and 443, utilizing the default NSE scripts for information gathering and vulnerability detection.
Example 2: Executing Specific Scripts:
nmap -sT -p 80 --script http-vuln-cve2014-3566 target.comThis command executes the http-vuln-cve2014-3566 script against target.com on port 80, specifically testing for the Heartbleed vulnerability.
Example 3: Specifying Multiple Scripts:
nmap -sV --script http-title,http-enum,http-useragent target.comThis command performs a scan against target.com, utilizing the http-title, http-enum, and http-useragent scripts to gather information about the website’s title, enumerate directories, and identify the user agent.
Frequently Asked Questions: Navigating the NSE Script Landscape
1. How do I find available NSE scripts?
The Nmap documentation provides a comprehensive list of available scripts, categorized by their purpose and functionality. Additionally, the nmap --script=all command displays all available scripts on the system.
2. Can I write my own NSE scripts?
Yes, users can write their own NSE scripts in Lua, tailoring them to specific needs and workflows. The Nmap documentation provides comprehensive guidance on scripting, including syntax, libraries, and best practices.
3. How do I update the NSE script library?
Nmap automatically updates the NSE script library upon installation. However, users can manually update the library by running the nmap --script-update command.
4. How can I troubleshoot NSE script errors?
NSE script errors are often displayed in the Nmap output. Users can refer to the Nmap documentation and online forums for troubleshooting tips and solutions. Additionally, enabling verbose output using the -v option can provide more detailed information about the script’s execution.
5. What are some best practices for using NSE scripts?
- Understand the script’s purpose and functionality before using it.
- Ensure the script is compatible with the target device and service.
- Use caution when executing scripts that modify the target system.
- Review the script’s output carefully and interpret the results accurately.
- Keep the NSE script library updated to benefit from new features and bug fixes.
Tips for Effective Utilization: Maximizing NSE Script Benefits
1. Leverage Default Scripts: Utilize the -sC option to run default scripts for comprehensive information gathering and vulnerability detection. This provides a solid foundation for further investigation.
2. Target Specific Scripts: Identify relevant scripts based on the scanning objective and target device. This ensures that the scan is efficient and relevant to the user’s needs.
3. Prioritize Vulnerability Detection: Utilize vulnerability detection scripts to proactively identify potential security risks. This allows for timely remediation and prevention of exploits.
4. Explore Custom Scripting: Develop custom NSE scripts to address specific requirements and workflows. This empowers users to tailor Nmap’s capabilities to their unique needs.
5. Stay Updated: Regularly update the NSE script library to benefit from new features, bug fixes, and improved functionality. This ensures that users have access to the latest and greatest tools for network scanning.
Conclusion: Embracing the Power of NSE Scripts
Nmap’s NSE scripting engine provides a powerful and flexible framework for extending its functionality beyond basic port scanning. By leveraging the wealth of available scripts and the ability to create custom solutions, users can significantly enhance their network exploration and security assessment capabilities. Understanding the benefits, implementation, and best practices associated with NSE scripts empowers users to utilize this powerful tool effectively, gaining valuable insights into network devices and services, proactively identifying vulnerabilities, and ultimately improving network security posture.




Closure
Thus, we hope this article has provided valuable insights into Exploring the Power of Nmap NSE Scripts: Expanding Network Scanning Capabilities. We hope you find this article informative and beneficial. See you in our next article!

