Navigating Memory Landscapes: A Comprehensive Guide to Memory-Mapped Files
Related Articles: Navigating Memory Landscapes: A Comprehensive Guide to Memory-Mapped Files
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Navigating Memory Landscapes: A Comprehensive Guide to Memory-Mapped Files. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Navigating Memory Landscapes: A Comprehensive Guide to Memory-Mapped Files
- 2 Introduction
- 3 Navigating Memory Landscapes: A Comprehensive Guide to Memory-Mapped Files
- 3.1 Memory Mapping: Bridging the Gap Between Memory and Files
- 3.2 Unmapping: Releasing Resources and Maintaining Integrity
- 3.3 Advantages and Disadvantages of Memory-Mapped Files
- 3.4 Practical Applications of Memory-Mapped Files
- 3.5 FAQs Regarding Memory-Mapped Files
- 3.6 Tips for Effective Memory-Mapped File Usage
- 3.7 Conclusion: Embracing the Power of Memory-Mapped Files
- 4 Closure
Navigating Memory Landscapes: A Comprehensive Guide to Memory-Mapped Files
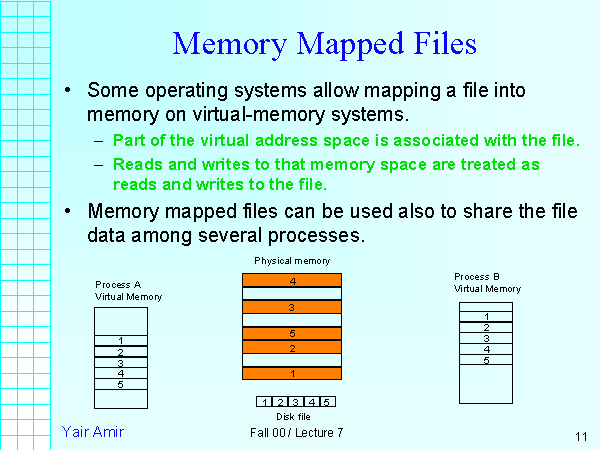
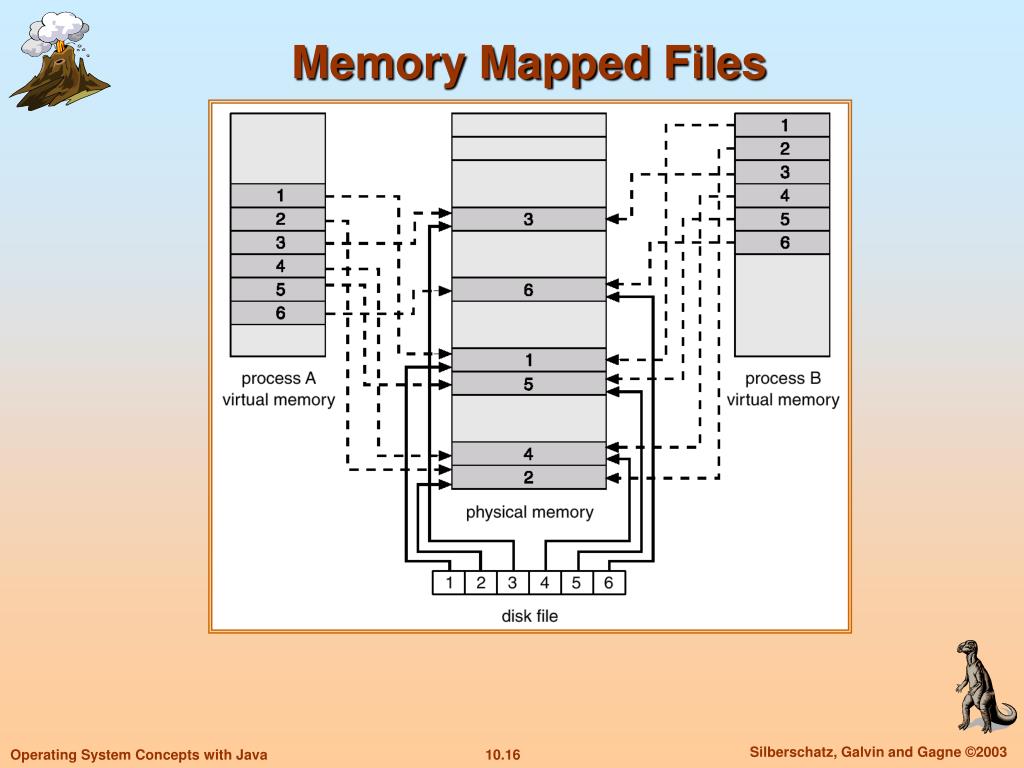
In the realm of computer science, efficient memory management is paramount. The ability to seamlessly access and manipulate data residing in both main memory and persistent storage plays a crucial role in optimizing application performance. Memory-mapped files, a powerful technique employed by operating systems, bridge this gap, allowing programs to treat files as if they were directly mapped into the process’s address space. This approach eliminates the need for explicit read and write operations, streamlining data access and enhancing program efficiency.
At the core of memory-mapped files lies the concept of memory mapping, a process that establishes a direct correspondence between a region of the file’s data and a specific area in the process’s virtual memory. This mapping enables programs to access and modify file data as if it were located in memory, eliminating the overhead associated with traditional file I/O operations. However, once the program has finished manipulating the file data, it becomes essential to unmap the file from memory, releasing the resources it occupied.
This article delves into the intricate world of memory-mapped files, exploring the nuances of memory mapping and unmapping, elucidating their advantages and disadvantages, and providing practical insights into their application.
Memory Mapping: Bridging the Gap Between Memory and Files
The act of memory mapping involves establishing a virtual address space within a process that directly corresponds to a specific region of a file residing on disk. This mapping essentially creates a virtual representation of the file within the process’s memory, allowing the program to treat the file as if it were a contiguous block of memory.
Key Concepts:
- Virtual Memory: A concept that allows programs to access memory that might not be physically present in RAM. This is achieved by using a page table that maps virtual addresses to physical addresses.
- File Descriptor: A unique identifier associated with an open file, used to interact with the file system.
- Mapping Region: The specific portion of the file that is mapped into memory.
- Mapped Memory Address: The virtual address range within the process’s address space that corresponds to the mapped file region.
The Process of Memory Mapping:
-
File Opening: The program opens the desired file using the appropriate system call (e.g.,
open()in Unix-like systems). - Mapping Request: The program requests the operating system to map a specified region of the file into its memory space. This request typically involves specifying the file descriptor, the starting offset within the file, the size of the region to be mapped, and the desired memory protection flags (e.g., read-only, read-write).
- Mapping Establishment: The operating system allocates a virtual address range within the process’s address space and creates a mapping between this range and the specified file region.
- Virtual Address Access: The program can now access the file data directly using the mapped memory address, as if it were located in memory.
Unmapping: Releasing Resources and Maintaining Integrity
Once the program has completed its operations on the mapped file, it becomes crucial to unmap the file from memory. This step is essential for several reasons:
- Resource Release: Unmapping frees up the virtual memory space occupied by the mapped file, making it available for other processes.
- Data Consistency: Unmapping ensures that any changes made to the mapped file are written back to disk, maintaining data integrity.
- Memory Management: Unmapping prevents memory leaks by releasing the resources associated with the mapped file.
The Process of Unmapping:
-
Unmapping Request: The program issues a system call (e.g.,
munmap()in Unix-like systems) to unmap the file from memory. This call typically requires the mapped memory address and the size of the region to be unmapped. - Mapping Removal: The operating system removes the mapping between the virtual address range and the file region, effectively detaching the file from the process’s memory.
- Resource Release: The virtual memory space previously occupied by the mapped file is released, and any associated resources are reclaimed by the system.
Advantages and Disadvantages of Memory-Mapped Files
Memory-mapped files offer several advantages, making them a valuable tool for optimizing application performance and simplifying data management:
- Simplified Data Access: By mapping files directly into memory, programs can access and manipulate file data without the overhead associated with traditional file I/O operations. This can significantly improve performance, especially when dealing with large files or frequent data access.
- Efficient Data Sharing: Memory-mapped files provide a mechanism for multiple processes to share the same data, eliminating the need for explicit data copying and synchronization. This can be particularly beneficial in scenarios involving inter-process communication or collaborative data editing.
- Reduced Memory Footprint: In some cases, memory-mapped files can actually reduce the overall memory footprint of an application. By mapping only the portion of the file that is actively being used, programs can avoid loading the entire file into memory, reducing memory consumption.
- Data Consistency: Memory-mapped files ensure that any changes made to the mapped data are automatically reflected in the underlying file, maintaining data consistency.
However, memory-mapped files also come with some potential disadvantages:
- Memory Overhead: Mapping a large file into memory can consume significant amounts of virtual memory, potentially impacting the performance of other processes.
- Data Security: Memory-mapped files can expose sensitive data to other processes that have access to the same virtual memory space. This can be a security concern if the data is confidential or requires protection.
- Complexity: Implementing memory-mapped file operations can be more complex than traditional file I/O, requiring a deeper understanding of memory management and virtual memory concepts.
Practical Applications of Memory-Mapped Files
Memory-mapped files find widespread use in various domains, including:
- Database Management: Memory-mapped files are often employed by database systems to manage large data files, allowing for efficient data access and manipulation.
- Image and Video Processing: Image and video processing applications often use memory-mapped files to load and process large multimedia files, leveraging the benefits of direct memory access.
- Scientific Computing: Scientific computing applications, involving complex calculations and large datasets, frequently employ memory-mapped files to manage data storage and access.
- Text Editing and Word Processing: Text editors and word processing applications may use memory-mapped files to manage large documents, enabling efficient editing and saving operations.
FAQs Regarding Memory-Mapped Files
1. How do memory-mapped files differ from traditional file I/O?
Traditional file I/O involves explicit read and write operations, where data is transferred between the file and memory. Memory-mapped files, on the other hand, treat the file as a contiguous block of memory, allowing programs to access and manipulate data directly without the overhead of traditional I/O operations.
2. What are the advantages of using memory-mapped files?
Memory-mapped files offer several advantages, including simplified data access, efficient data sharing, reduced memory footprint, and data consistency.
3. What are the disadvantages of using memory-mapped files?
Potential disadvantages include memory overhead, data security concerns, and complexity in implementation.
4. When should I use memory-mapped files?
Memory-mapped files are particularly beneficial for applications that require frequent access to large files, efficient data sharing, or data consistency.
5. How do I unmap a memory-mapped file?
To unmap a memory-mapped file, you need to use the appropriate system call (e.g., munmap() in Unix-like systems), providing the mapped memory address and the size of the region to be unmapped.
6. What happens if a program crashes while using a memory-mapped file?
If a program crashes while using a memory-mapped file, the operating system will typically handle the cleanup process, ensuring that any changes made to the file are written back to disk. However, depending on the specific circumstances, data corruption or loss might occur.
7. Are memory-mapped files suitable for all applications?
Memory-mapped files are not suitable for all applications. They are most beneficial when dealing with large files, frequent data access, or scenarios where data consistency is critical. However, for applications that prioritize data security or have limited memory resources, alternative approaches might be more appropriate.
Tips for Effective Memory-Mapped File Usage
- Optimize Mapping Size: Avoid mapping unnecessarily large portions of the file into memory, as this can lead to excessive memory consumption. Instead, map only the regions that are actively being used.
- Use Memory Protection Flags: Utilize appropriate memory protection flags (e.g., read-only, read-write) to ensure data integrity and prevent accidental modifications.
- Handle Errors Gracefully: Implement robust error handling mechanisms to deal with potential failures during mapping, unmapping, or file access.
- Consider Alternative Approaches: If data security is a major concern, or if memory resources are limited, consider alternative approaches, such as traditional file I/O or database management systems.
Conclusion: Embracing the Power of Memory-Mapped Files
Memory-mapped files, by seamlessly bridging the gap between memory and persistent storage, offer a powerful and efficient mechanism for managing data in modern applications. Their ability to simplify data access, enhance performance, and facilitate data sharing makes them an invaluable tool for a wide range of applications. However, it is essential to understand the potential disadvantages and implement best practices to ensure optimal performance, data integrity, and security. By leveraging the power of memory-mapped files while adhering to sound principles, developers can unlock new levels of efficiency and effectiveness in their applications, navigating the memory landscape with confidence.

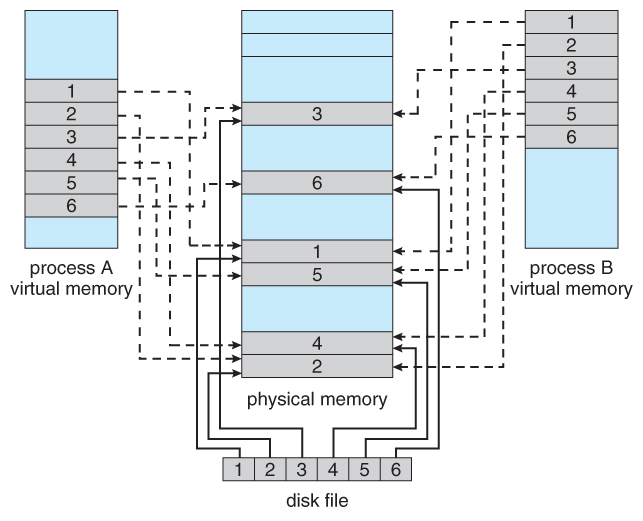



Closure
Thus, we hope this article has provided valuable insights into Navigating Memory Landscapes: A Comprehensive Guide to Memory-Mapped Files. We hope you find this article informative and beneficial. See you in our next article!
