Unlocking Network Insights: A Comprehensive Guide to Nmap Scripting
Related Articles: Unlocking Network Insights: A Comprehensive Guide to Nmap Scripting
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Unlocking Network Insights: A Comprehensive Guide to Nmap Scripting. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unlocking Network Insights: A Comprehensive Guide to Nmap Scripting

Nmap, the Network Mapper, is a powerful tool for network discovery and security auditing. Beyond its core functionality of port scanning, Nmap offers a vast library of scripts that extend its capabilities, enabling users to gather deeper insights into target systems. These scripts, written in Lua, automate various tasks, from detecting specific vulnerabilities to identifying running services and gathering information about operating systems.
This article delves into the world of Nmap scripting, exploring how to leverage its full potential for comprehensive network analysis.
Understanding Nmap Scripts
Nmap scripts are modular components that can be executed alongside port scans, adding an extra layer of information gathering to the process. They operate by interacting with target services through various techniques, including:
- Service Interaction: Scripts can send custom requests to services, analyzing the responses for vulnerabilities, versions, and other valuable information.
- Banner Grabbing: Scripts can extract and analyze service banners, providing clues about the running application, version, and potentially even security configurations.
- OS Fingerprinting: Scripts can exploit specific characteristics of operating systems to identify the underlying platform.
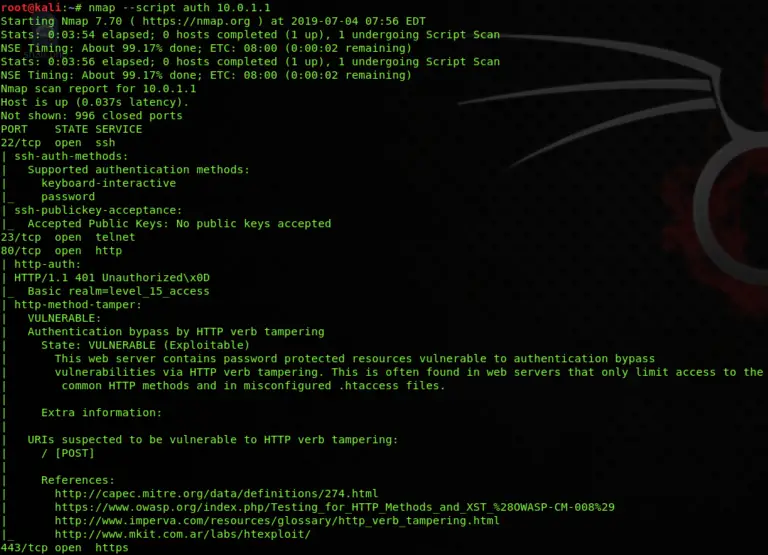
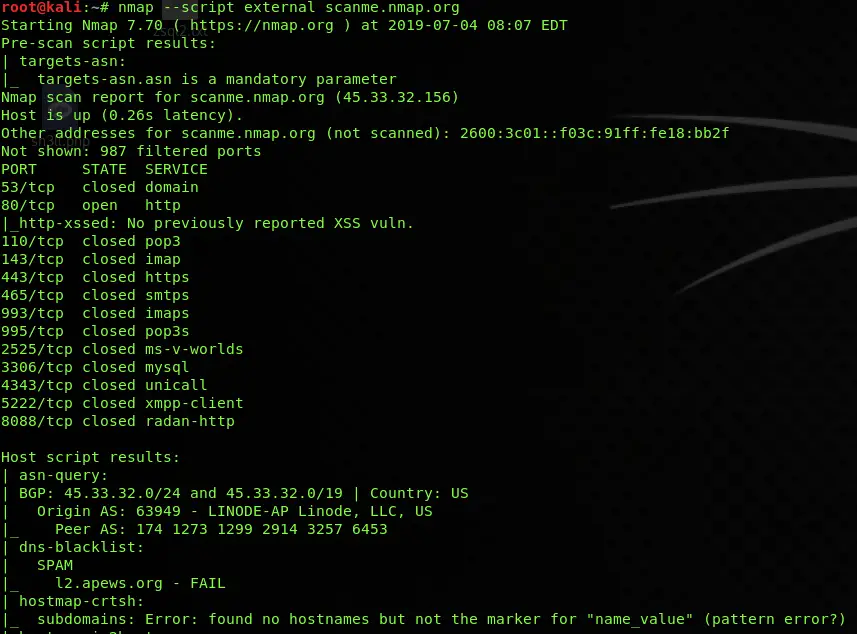
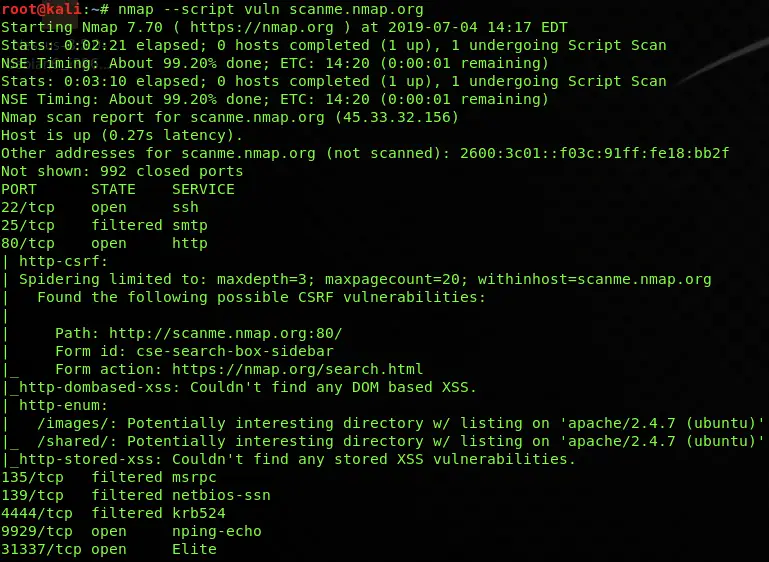
- Vulnerability Detection: Some scripts are specifically designed to detect known vulnerabilities, allowing for proactive security assessments.
Leveraging the Power of Nmap Scripting
Nmap scripts offer a wide range of benefits, making them invaluable for network administrators, security professionals, and researchers:
- Automated Information Gathering: Scripts automate repetitive tasks, saving time and effort. This allows for rapid assessment of large networks, identifying potential security risks and vulnerabilities.
- Enhanced Network Visibility: Scripts provide a deeper understanding of target systems beyond basic port scanning. They reveal hidden services, identify operating systems, and uncover potential vulnerabilities, offering a more complete picture of the network landscape.
- Proactive Security Assessment: Scripts enable proactive vulnerability detection, allowing for early identification and remediation of security flaws before they can be exploited.
- Customizable Analysis: The vast library of Nmap scripts allows users to tailor their analysis to specific needs. Whether focusing on web servers, network devices, or specific vulnerabilities, there’s likely a script to meet the requirement.
Exploring Nmap’s Script Library
Nmap comes with a comprehensive library of over 700 scripts, categorized into various modules:
- Default: These scripts are automatically executed during port scans, providing basic information about services, versions, and operating systems.
- Discovery: Scripts in this module focus on discovering hosts and services on the network.
- Exploit: These scripts attempt to exploit known vulnerabilities to gain access to systems.
- Vulnerability: Scripts designed to detect specific vulnerabilities and weaknesses.
- Auth: Scripts related to authentication, including brute-force attacks and password recovery attempts.
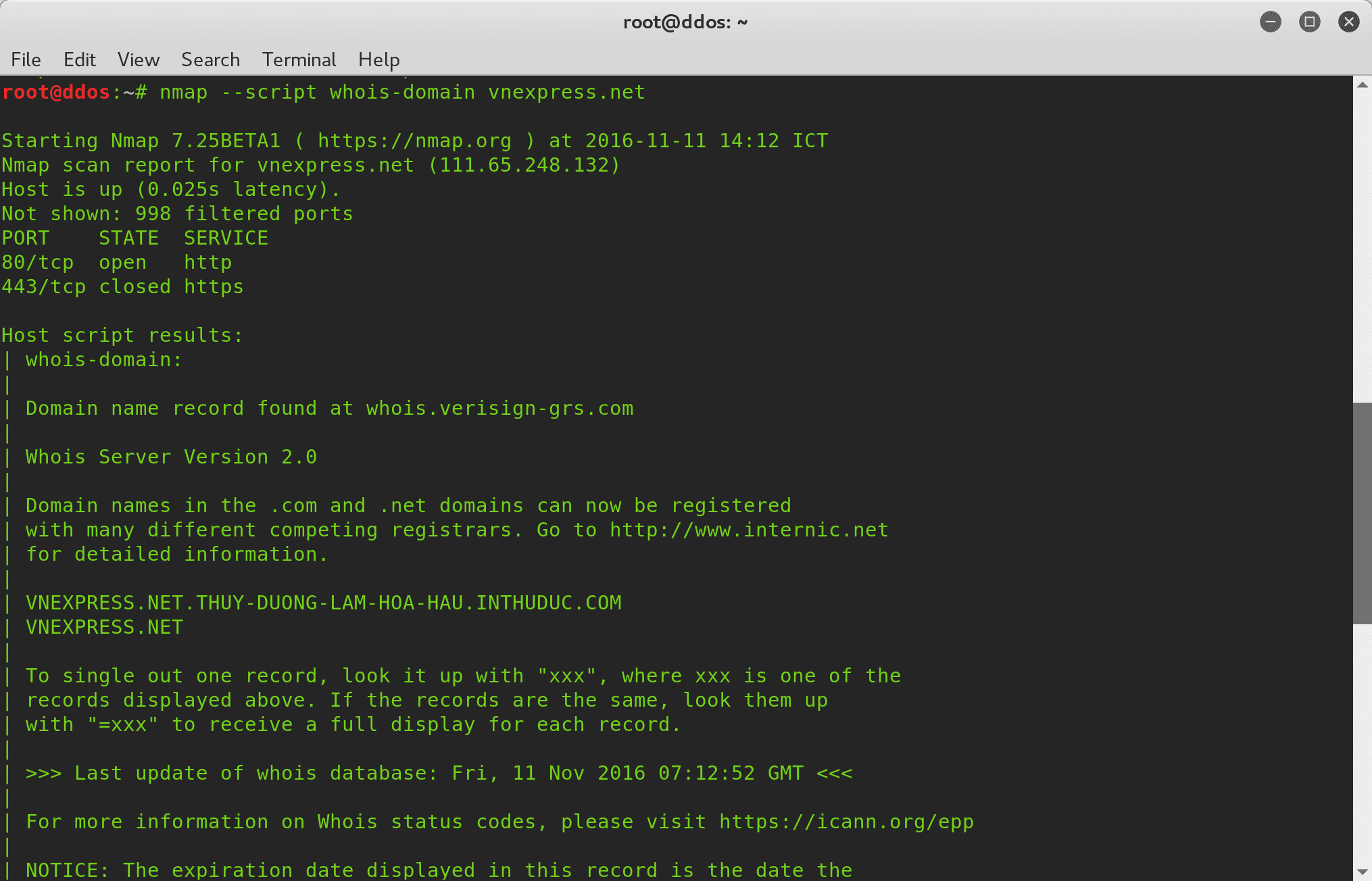
- Auxiliary: Scripts that perform various miscellaneous tasks, such as banner grabbing, OS fingerprinting, and service enumeration.
Running Nmap Scripts: A Practical Guide
Nmap offers several ways to execute scripts, allowing for flexible and customized scanning:
-
The
--scriptOption: This option allows users to specify individual scripts or script categories to run alongside a port scan. -
The
--script-argsOption: This option allows users to pass arguments to specific scripts, customizing their behavior and output. -
The
--script-helpOption: This option provides detailed information about individual scripts, including their purpose, arguments, and output. -
The
-sCOption: This option executes all scripts in the default category, providing basic information about services, versions, and operating systems.
Example: Identifying Vulnerable Services
The following command uses the --script option to execute the vuln-cve-2021-44228 script, which checks for the Log4j vulnerability:
nmap -sV -p 8080 --script vuln-cve-2021-44228 target.comThis command will scan port 8080 on target.com and execute the vuln-cve-2021-44228 script to identify any potential Log4j vulnerabilities.
FAQs: Demystifying Nmap Scripting
1. How do I find the right script for my needs?
Nmap provides a comprehensive script database accessible through the --script-help option. The database includes detailed descriptions, arguments, and output examples for each script. Additionally, online resources like the Nmap Scripting Wiki and the Nmap Scripting Archive offer valuable information and examples.
2. Can I create my own Nmap scripts?
Yes, Nmap scripts are written in Lua, a lightweight scripting language. The Nmap documentation provides detailed guidance on script development, including examples and tutorials.
3. How can I ensure the scripts are reliable?
Nmap scripts are developed and maintained by a community of security researchers and developers. However, it’s always recommended to verify the reliability of a script before using it in production environments. Consult online forums, security blogs, and reputable sources for information about script accuracy and potential risks.
4. Are there any security risks associated with running Nmap scripts?
While Nmap scripts are designed to be safe, some scripts may perform actions that could potentially be considered intrusive or malicious. It’s crucial to understand the purpose and potential impact of each script before executing it. Always obtain proper authorization before scanning any network or system.
Tips for Effective Nmap Scripting
-
Start with the
-sCoption: This option executes all default scripts, providing a good baseline understanding of the target system. -
Use the
--script-helpoption: This option provides detailed information about individual scripts, helping you choose the most relevant ones for your needs. - Test scripts in controlled environments: Before using scripts in production environments, test them on non-critical systems to ensure they function as expected and do not cause unintended consequences.
- Keep scripts updated: Nmap’s script library is constantly evolving, with new scripts being added and existing ones being updated. Ensure you’re using the latest versions for optimal results.
Conclusion
Nmap scripting offers a powerful and versatile approach to network analysis, enabling users to gather deeper insights into target systems and identify potential vulnerabilities. By leveraging the vast library of Nmap scripts and understanding their capabilities, network administrators, security professionals, and researchers can gain a more comprehensive understanding of their network environments and proactively address security risks. Nmap scripting is a valuable tool for anyone seeking to enhance network visibility, improve security posture, and optimize network operations.
![Find Network Vulnerabilities with Nmap Scripts [Tutorial] - YouTube](https://i.ytimg.com/vi/3U1pJ-eJrAU/maxresdefault.jpg)


Closure
Thus, we hope this article has provided valuable insights into Unlocking Network Insights: A Comprehensive Guide to Nmap Scripting. We appreciate your attention to our article. See you in our next article!
