Unlocking Network Insights: Leveraging Nmap’s Scripting Capabilities for Comprehensive Scanning
Related Articles: Unlocking Network Insights: Leveraging Nmap’s Scripting Capabilities for Comprehensive Scanning
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Unlocking Network Insights: Leveraging Nmap’s Scripting Capabilities for Comprehensive Scanning. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unlocking Network Insights: Leveraging Nmap’s Scripting Capabilities for Comprehensive Scanning
Nmap, the Network Mapper, is a powerful tool used for network discovery and security auditing. Beyond its core functionality of port scanning, Nmap offers a rich scripting engine that allows users to extend its capabilities significantly. This scripting engine enables the execution of custom scripts, providing in-depth information about target systems and services.
Understanding Nmap’s Scripting Engine:
Nmap’s scripting engine is a versatile tool that allows users to automate network analysis tasks and gather valuable information beyond basic port scanning. These scripts, written in the Lua programming language, can interact with target systems in various ways, including:
- Service and Version Detection: Scripts can probe services running on target ports and identify their versions, potentially revealing vulnerabilities or outdated software.
- Vulnerability Detection: Scripts can test for known vulnerabilities, such as common exploits or misconfigurations, providing early warning signs of security risks.
- Operating System Fingerprinting: Scripts can analyze network responses to identify the operating system running on target devices, aiding in network segmentation and security planning.
- Network Service Enumeration: Scripts can enumerate services and their associated configurations, providing detailed information about the network infrastructure.
- Custom Functionality: Users can create their own scripts to perform specific tasks tailored to their needs, such as checking for specific protocols or analyzing network traffic patterns.
Benefits of Utilizing Nmap Scripts:
Employing Nmap scripts offers several advantages, including:
- Enhanced Network Visibility: Scripts provide a deeper understanding of network infrastructure, revealing hidden services and vulnerabilities that may be missed by basic port scanning.
- Automated Vulnerability Assessment: Scripts automate the process of testing for known vulnerabilities, saving time and effort compared to manual checks.
- Improved Security Posture: By identifying vulnerabilities and misconfigurations, scripts enable proactive security measures to be implemented, reducing the risk of attacks.
- Streamlined Network Analysis: Scripts can automate repetitive tasks, allowing security professionals to focus on more complex analyses and strategic decisions.
- Increased Efficiency: Scripts can perform tasks quickly and efficiently, providing faster insights and enabling faster response times to potential threats.
Running Multiple Scripts with Nmap:
Nmap provides various methods for running multiple scripts simultaneously, enhancing the efficiency of network analysis. The most common methods include:
-
The
-sCOption: This option executes the default set of Nmap scripts, which includes a broad range of scripts for common tasks such as version detection, vulnerability scanning, and operating system fingerprinting. -
The
-sTOption: This option executes a specific set of scripts defined in a script database file. Users can customize this database file to include their preferred scripts or create their own script sets for specific purposes. -
The
--scriptOption: This option allows users to specify individual scripts to be executed, providing fine-grained control over the scanning process. -
The
--script-argsOption: This option allows users to pass arguments to specific scripts, customizing their behavior and providing additional context for the analysis.
Example Usage:
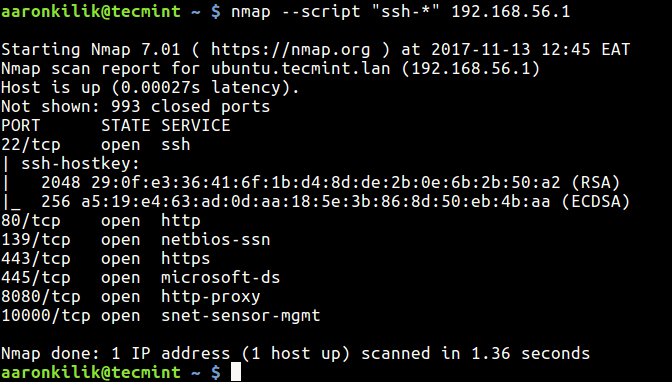
To run a specific set of scripts, including http-title and http-enum, against a target host with an IP address of 192.168.1.100, the following Nmap command can be used:
nmap -sT --script=http-title,http-enum 192.168.1.100Frequently Asked Questions (FAQs):
Q: What are some common Nmap scripts and their uses?
A: Nmap offers a vast library of scripts covering various aspects of network analysis. Some common scripts include:
-
http-title: Retrieves the title of a web page, potentially revealing the website’s name or purpose. -
http-enum: Enumerates directories and files on a web server, providing insights into the website’s structure and content. -
ftp-anon: Attempts to access an FTP server anonymously, identifying potential vulnerabilities or misconfigurations. -
smb-enum-users: Enumerates users and shares on a Samba server, potentially revealing sensitive information. -
ssl-cert: Retrieves the SSL/TLS certificate from a web server, allowing for analysis of certificate validity and trust.
Q: How can I create my own Nmap scripts?
A: Creating custom Nmap scripts requires familiarity with the Lua programming language. Nmap’s documentation provides comprehensive resources and examples for script development. The Nmap Scripting Guide offers a detailed explanation of the scripting language and its capabilities, while the Nmap Script Library showcases a variety of existing scripts that can serve as inspiration for new creations.
Q: What are some best practices for utilizing Nmap scripts?
A: When using Nmap scripts, it is important to follow best practices to ensure responsible and effective analysis:
- Understand Script Functionality: Before running a script, thoroughly review its documentation to understand its purpose, potential risks, and expected output.
- Avoid Unnecessary Scripting: Only use scripts that are relevant to your specific needs and avoid running unnecessary scripts that could potentially disrupt network operations.
- Respect Network Policies: Ensure that your scripting activities comply with network policies and ethical hacking guidelines.
- Use Caution with Sensitive Information: Be mindful of sensitive information that may be revealed by scripts, such as user credentials or confidential data.
- Regularly Update Scripts: Keep Nmap and its scripts updated to ensure compatibility and access to the latest security features.
Tips for Effective Nmap Scripting:
- Prioritize Script Selection: Choose scripts that are relevant to your specific goals and avoid unnecessary scripting.
-
Customize Script Arguments: Utilize the
--script-argsoption to pass arguments to scripts, tailoring their behavior to your needs. - Combine Scripting with Other Nmap Features: Integrate scripting with other Nmap features, such as port scanning and operating system fingerprinting, for a comprehensive analysis.
- Document Script Usage: Maintain clear documentation of scripts used, including their purpose, arguments, and expected output.
- Experiment and Learn: Explore the vast library of Nmap scripts and experiment with different combinations to discover new insights and enhance your network analysis skills.
Conclusion:
Nmap’s scripting engine empowers network security professionals and researchers to go beyond basic port scanning and gain deeper insights into network infrastructure. By leveraging the power of scripting, users can automate tasks, identify vulnerabilities, and enhance their network security posture. Implementing best practices and exploring the vast library of scripts available can significantly improve the effectiveness of network analysis, leading to more informed decisions and proactive security measures.





Closure
Thus, we hope this article has provided valuable insights into Unlocking Network Insights: Leveraging Nmap’s Scripting Capabilities for Comprehensive Scanning. We appreciate your attention to our article. See you in our next article!
