Unlocking the Secrets of SMB: A Comprehensive Guide to Nmap’s Scripting Capabilities
Related Articles: Unlocking the Secrets of SMB: A Comprehensive Guide to Nmap’s Scripting Capabilities
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Unlocking the Secrets of SMB: A Comprehensive Guide to Nmap’s Scripting Capabilities. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Unlocking the Secrets of SMB: A Comprehensive Guide to Nmap’s Scripting Capabilities
- 2 Introduction
- 3 Unlocking the Secrets of SMB: A Comprehensive Guide to Nmap’s Scripting Capabilities
- 3.1 The Power of Nmap Scripts for SMB
- 3.2 Exploring Nmap’s SMB Scripting Capabilities
- 3.3 Frequently Asked Questions (FAQs)
- 3.4 Tips for Effective SMB Scripting with Nmap
- 3.5 Conclusion
- 4 Closure
Unlocking the Secrets of SMB: A Comprehensive Guide to Nmap’s Scripting Capabilities

The Server Message Block (SMB) protocol is a ubiquitous component of network infrastructure, facilitating file and printer sharing across Windows-based systems. However, its very ubiquity makes it a prime target for malicious actors seeking to exploit vulnerabilities. Understanding the security posture of SMB services is paramount, and this is where Nmap’s scripting capabilities shine.
Nmap, the network mapper, is a powerful tool for network reconnaissance and security auditing. Beyond its traditional port scanning functions, Nmap offers a rich library of scripts that can be leveraged to probe specific services, identify vulnerabilities, and even attempt to exploit weaknesses. For SMB services, Nmap’s scripting arsenal provides a comprehensive suite of tools for gaining valuable insights and bolstering security.
The Power of Nmap Scripts for SMB
Nmap scripts are small programs written in Lua that automate specific tasks related to network services. They enable users to:
- Identify running services: Nmap scripts can detect SMB services, their versions, and specific configurations, providing a comprehensive overview of the SMB environment.
- Discover vulnerabilities: Scripts like "smb-vuln-cve2017-7494" and "smb-vuln-ms17-010" can identify known exploits and vulnerabilities in SMB services, allowing for proactive mitigation.
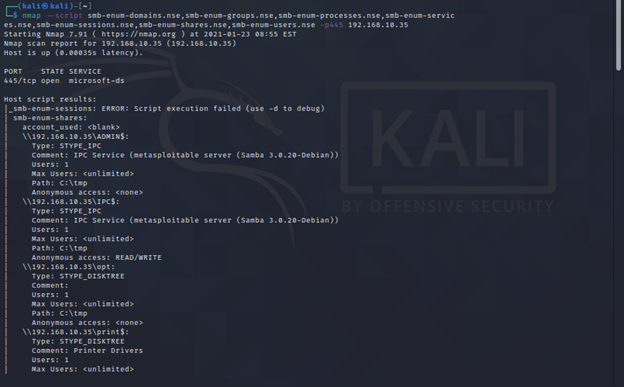
- Test for weak configurations: Nmap scripts can assess the security of SMB shares, identifying weak permissions, insecure authentication methods, and potentially vulnerable settings.
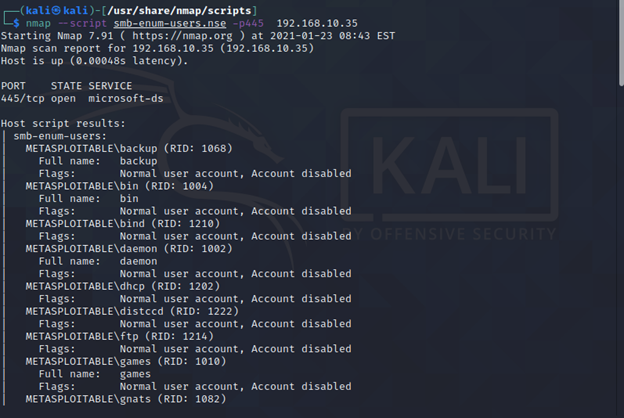
- Gather valuable information: Scripts can gather details like user names, share names, and file system structures, providing valuable reconnaissance data.
- Automate repetitive tasks: Nmap scripts streamline the process of security auditing, reducing manual effort and enabling efficient analysis of large networks.
Exploring Nmap’s SMB Scripting Capabilities
To effectively utilize Nmap’s SMB scripting capabilities, it is essential to understand the structure and syntax of the scripts. Nmap scripts are typically categorized into various families, each focusing on specific functionalities.
SMB-Specific Script Families:
- smb-enum: Scripts in this family focus on enumerating SMB shares, users, and other resources. Examples include "smb-enum-shares", "smb-enum-users", and "smb-enum-groups".
- smb-vuln: This family contains scripts designed to identify known vulnerabilities in SMB services. Examples include "smb-vuln-ms17-010" (EternalBlue), "smb-vuln-cve-2017-7494", and "smb-vuln-cve-2017-11882".
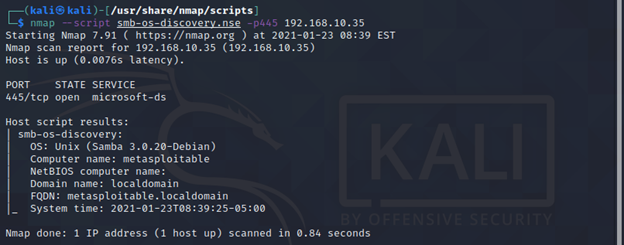
- smb-os: These scripts aim to identify the operating system of the SMB server and its specific version. Examples include "smb-os-discovery" and "smb-os-fingerprint".
- smb-brute: This family contains scripts for attempting brute force attacks against SMB services, aiming to discover weak passwords or authentication vulnerabilities.
Example Script Usage:
nmap -sV -p 445 --script smb-enum-shares,smb-vuln-ms17-010 192.168.1.100This command instructs Nmap to scan the target host 192.168.1.100 on port 445 (SMB), perform version detection (-sV), and run the "smb-enum-shares" and "smb-vuln-ms17-010" scripts. The results will provide information about the shares available on the target host and whether it is vulnerable to the EternalBlue exploit.
Frequently Asked Questions (FAQs)
Q: What are the benefits of using Nmap scripts for SMB security auditing?
A: Nmap scripts provide a comprehensive and automated approach to SMB security assessment, enabling:
- Early detection of vulnerabilities: Scripts can identify known exploits and weaknesses before they are exploited by malicious actors.
- Improved security posture: By identifying vulnerabilities and weak configurations, organizations can implement appropriate security measures to mitigate risks.
- Reduced time and effort: Nmap scripts automate tasks, saving time and resources compared to manual auditing methods.
- Enhanced visibility: Scripts provide detailed information about SMB services, including versions, configurations, and vulnerabilities.
Q: How do I find the right Nmap script for my needs?
A: Nmap provides a comprehensive script library with detailed documentation. The nmap --script=help command displays a list of all available scripts, while nmap --script=help smb lists scripts specifically designed for SMB services.
Q: What are the limitations of Nmap scripts for SMB security auditing?
A: Nmap scripts are a valuable tool but have limitations:
- Limited to known vulnerabilities: Scripts primarily target known vulnerabilities, leaving unknown or zero-day exploits undetected.
- False positives: Some scripts may produce false positives, requiring manual verification of results.
- Potential for disruption: Aggressive scripting can potentially disrupt network operations, requiring careful consideration of scan settings.
Tips for Effective SMB Scripting with Nmap
-
Start with basic scanning: Use
nmap -sV -p 445to identify SMB services and their versions before running specific scripts. - Use script families strategically: Focus on relevant script families like "smb-enum" for reconnaissance and "smb-vuln" for vulnerability detection.
- Prioritize known vulnerabilities: Use scripts like "smb-vuln-ms17-010" and "smb-vuln-cve-2017-7494" to check for critical exploits.
- Review and verify results: Carefully analyze script outputs and manually verify suspicious findings to avoid false positives.
- Use appropriate scan settings: Optimize scan settings for speed and accuracy, considering network constraints and potential impact on services.
- Stay updated with Nmap and scripts: Regularly update Nmap and its script library to benefit from new features and vulnerability detection capabilities.
Conclusion
Nmap’s scripting capabilities offer a powerful and versatile tool for analyzing SMB services, identifying vulnerabilities, and improving network security. By leveraging the comprehensive library of SMB-specific scripts, security professionals can gain valuable insights into their SMB environment, proactively mitigate risks, and enhance the overall security posture of their network infrastructure. While Nmap scripts provide a valuable starting point, it is crucial to remember that they are just one piece of the puzzle. Comprehensive security assessments should incorporate a multi-faceted approach, including manual analysis, penetration testing, and continuous monitoring.

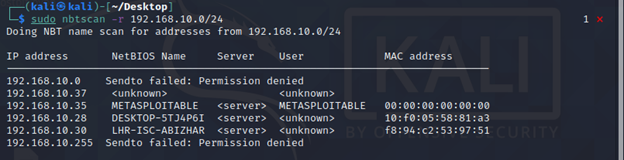

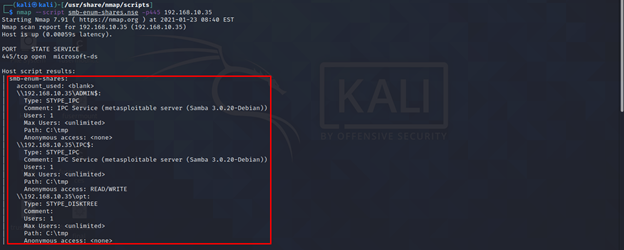
Closure
Thus, we hope this article has provided valuable insights into Unlocking the Secrets of SMB: A Comprehensive Guide to Nmap’s Scripting Capabilities. We appreciate your attention to our article. See you in our next article!
