Unveiling Hidden Information: A Comprehensive Guide to Nmap Scripting
Related Articles: Unveiling Hidden Information: A Comprehensive Guide to Nmap Scripting
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Unveiling Hidden Information: A Comprehensive Guide to Nmap Scripting. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Unveiling Hidden Information: A Comprehensive Guide to Nmap Scripting
- 2 Introduction
- 3 Unveiling Hidden Information: A Comprehensive Guide to Nmap Scripting
- 3.1 Exploring the Power of Default Scripts
- 3.2 Unleashing the Potential: Nmap Scripting in Action
- 3.3 Beyond the Basics: Fine-Tuning Script Execution
- 3.4 FAQ: Understanding Nmap Scripting
- 3.5 Tips for Effective Scripting
- 3.6 Conclusion: Empowering Network Security with Nmap Scripting
- 4 Closure
Unveiling Hidden Information: A Comprehensive Guide to Nmap Scripting

Nmap, the Network Mapper, is a powerful tool for network exploration and security auditing. While its core functionality lies in port scanning, Nmap’s versatility extends far beyond, encompassing a robust scripting engine that allows for in-depth analysis and discovery of vulnerabilities. This scripting capability, often referred to as "Nmap Scripting Engine" (NSE), empowers users to automate complex tasks, gather detailed information, and uncover hidden aspects of target systems.
At the heart of NSE lies a library of pre-written scripts, each designed to perform a specific function. These scripts, known as "default scripts," offer a streamlined approach to gathering valuable data without the need for manual scripting. By utilizing these scripts, security professionals and network administrators can gain a deeper understanding of target systems, identify potential security weaknesses, and enhance their overall security posture.
Exploring the Power of Default Scripts
Nmap’s default scripts encompass a wide range of functionalities, covering areas such as:
- Service and Version Detection: Scripts can accurately identify running services and their versions, providing insights into the software running on target systems. This information is crucial for vulnerability assessment, as outdated software often harbors security flaws.
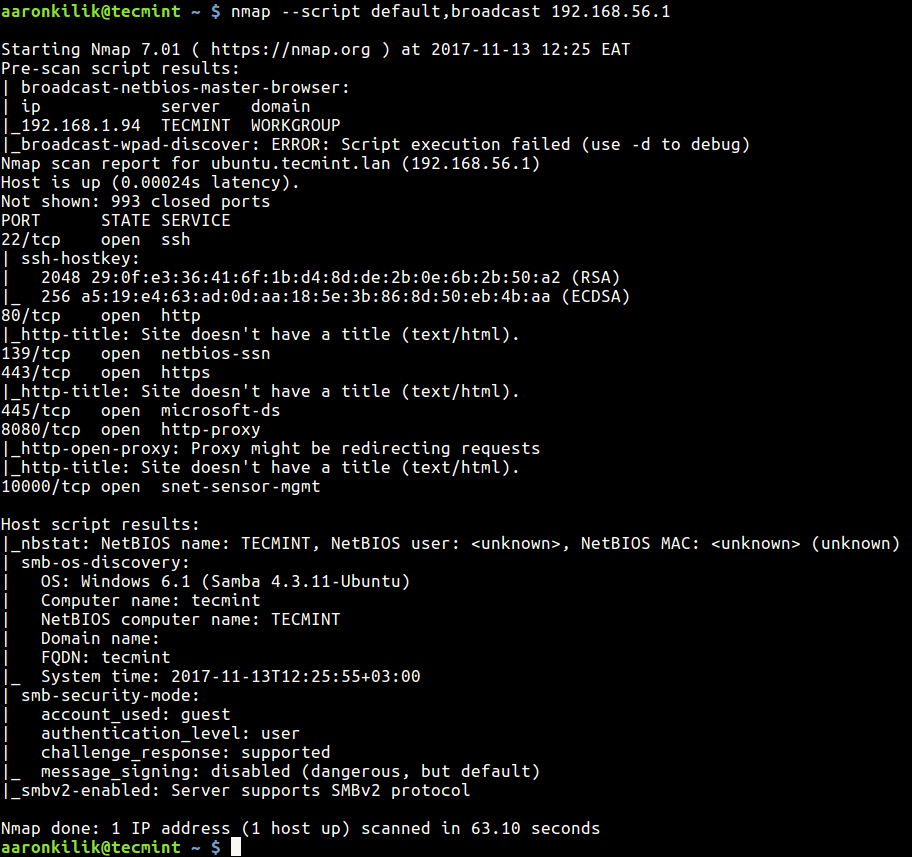
- Operating System Detection: Scripts can determine the operating system running on a target, even if it attempts to hide its identity. This knowledge is valuable for tailoring security measures and understanding potential vulnerabilities specific to the operating system.
- Vulnerability Scanning: Scripts can check for known vulnerabilities in services and applications, revealing potential entry points for attackers. This proactive approach helps mitigate risks before they are exploited.
- Network Discovery: Scripts can identify devices on a network, discover hidden hosts, and map network topology, providing a comprehensive understanding of the network infrastructure.
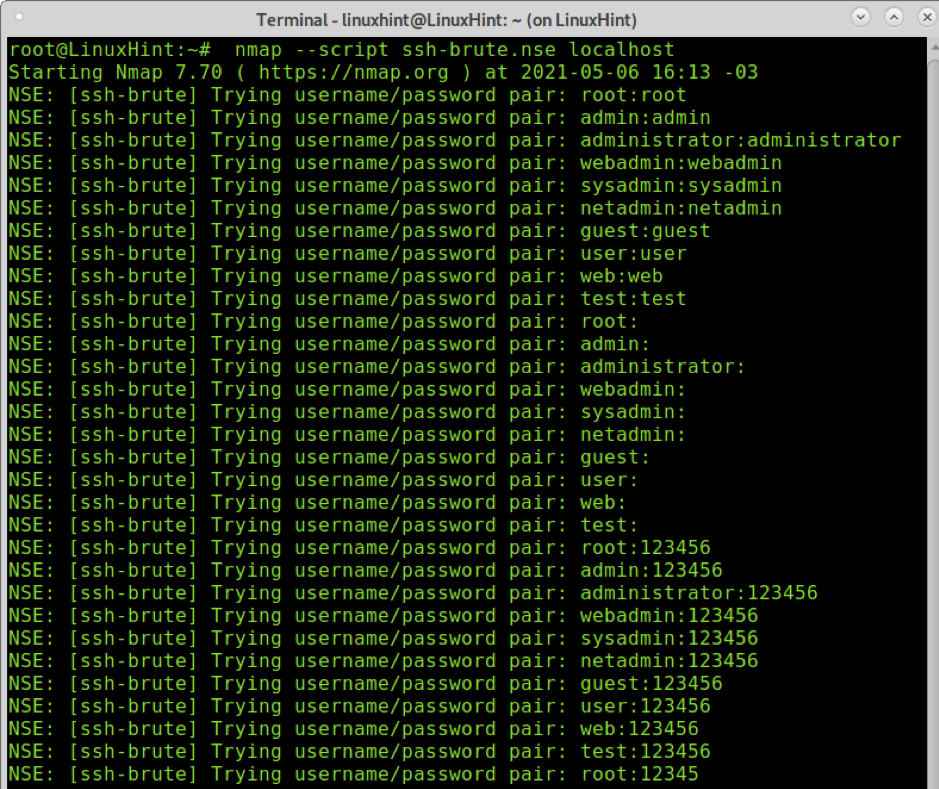
- Credential Gathering: Scripts can attempt to retrieve credentials from vulnerable services, revealing potential weak points in security practices.
Unleashing the Potential: Nmap Scripting in Action
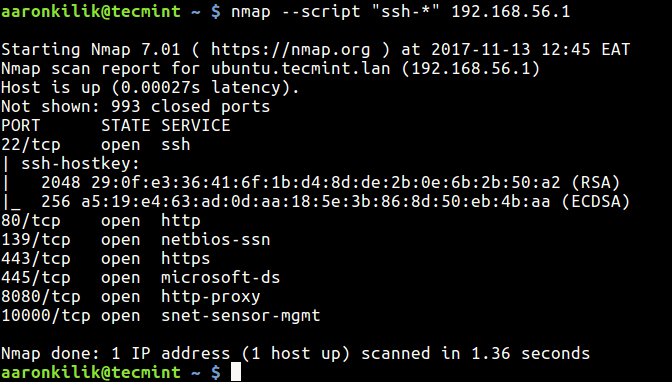
To leverage the power of Nmap’s default scripts, users can simply include the -sC option in their Nmap commands. This option instructs Nmap to execute all default scripts against the target systems.
Example:
nmap -sC -p 80,443 192.168.1.1This command will scan the IP address 192.168.1.1 on ports 80 and 443, executing all default scripts to gather comprehensive information about the target system.
Beyond the Basics: Fine-Tuning Script Execution
Nmap’s scripting engine provides flexibility for tailoring script execution to specific needs. Users can:
-
Select Specific Scripts: Instead of running all default scripts, users can choose specific scripts by name using the
-sCoption followed by the script names.Example:
nmap -sC http-title,http-server-header 192.168.1.1This command will run only the
http-titleandhttp-server-headerscripts against the target system. -
Disable Scripts: Users can disable specific scripts using the
--script-excludeoption followed by a comma-separated list of script names.Example:
nmap -sC --script-exclude http-title,http-server-header 192.168.1.1This command will run all default scripts except
http-titleandhttp-server-header. -
Modify Script Options: Many scripts offer options to customize their behavior. These options can be specified using the
--script-argsoption followed by the script name and the desired options.Example:
nmap -sC --script-args http-enum.url=www.example.com 192.168.1.1This command will run the
http-enumscript with theurloption set towww.example.com.
FAQ: Understanding Nmap Scripting
Q: What are the benefits of using Nmap default scripts?
A: Using default scripts offers significant advantages:
- Increased Efficiency: Scripts automate tasks, saving time and effort compared to manual analysis.
- Enhanced Information Gathering: Scripts provide detailed information that might be difficult or time-consuming to gather manually.
- Improved Security Posture: By identifying vulnerabilities and potential attack vectors, scripts help strengthen security measures.
Q: How do I find out which default scripts are available?
A: Nmap provides a comprehensive list of default scripts with detailed descriptions. This information can be accessed through the nmap --script-list command.
Q: How do I learn more about specific scripts?
A: Detailed documentation for each script is available in the Nmap documentation. This documentation includes descriptions, usage examples, and available options.
Q: Are default scripts enough for comprehensive security assessments?
A: While default scripts provide a solid foundation for security assessments, they may not cover all potential vulnerabilities. It is often necessary to supplement default scripts with custom scripts or specialized tools for more in-depth analysis.
Q: How can I contribute to the Nmap scripting library?
A: Nmap welcomes contributions from the security community. If you have expertise in scripting or have developed valuable scripts, consider contributing to the Nmap scripting library.
Tips for Effective Scripting
- Start with Default Scripts: Begin by using default scripts to gain a baseline understanding of target systems.
- Focus on Relevant Scripts: Select scripts based on your specific needs and the type of information you seek.
- Explore Script Options: Utilize script options to fine-tune script behavior and customize data gathering.
- Combine with Other Nmap Features: Integrate scripting with other Nmap features, such as port scanning and OS detection, for a comprehensive analysis.
- Stay Updated: Regularly check for new or updated scripts to ensure you have access to the latest capabilities.
Conclusion: Empowering Network Security with Nmap Scripting
Nmap’s default scripts offer a powerful and versatile tool for security professionals and network administrators. By leveraging these pre-written scripts, users can gain deeper insights into target systems, identify potential vulnerabilities, and enhance their overall security posture. As the security landscape evolves, Nmap’s scripting engine remains a crucial tool for staying ahead of emerging threats and safeguarding networks against malicious activity.




Closure
Thus, we hope this article has provided valuable insights into Unveiling Hidden Information: A Comprehensive Guide to Nmap Scripting. We thank you for taking the time to read this article. See you in our next article!
