Unveiling Network Vulnerabilities: A Comprehensive Guide to Nmap Scripting
Related Articles: Unveiling Network Vulnerabilities: A Comprehensive Guide to Nmap Scripting
Introduction
With great pleasure, we will explore the intriguing topic related to Unveiling Network Vulnerabilities: A Comprehensive Guide to Nmap Scripting. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Unveiling Network Vulnerabilities: A Comprehensive Guide to Nmap Scripting
- 2 Introduction
- 3 Unveiling Network Vulnerabilities: A Comprehensive Guide to Nmap Scripting
- 3.1 The Power of Nmap Scripting
- 3.2 Exploring the Scripting Landscape
- 3.3 Implementing Nmap Scripts: A Practical Guide
- 3.4 Leveraging Scripting for Enhanced Security Assessments
- 3.5 FAQs: Addressing Common Questions
- 3.6 Tips for Effective Scripting
- 3.7 Conclusion
- 4 Closure
Unveiling Network Vulnerabilities: A Comprehensive Guide to Nmap Scripting
![Find Network Vulnerabilities with Nmap Scripts [Tutorial] - YouTube](https://i.ytimg.com/vi/3U1pJ-eJrAU/maxresdefault.jpg)
Network security is an ever-evolving landscape, constantly adapting to new threats and vulnerabilities. The ability to identify and assess these vulnerabilities is crucial for any organization seeking to protect its digital assets. Network Mapper (Nmap), a powerful open-source tool, provides a versatile framework for network exploration and security auditing. This article delves into the realm of Nmap scripting, specifically focusing on its capabilities in uncovering network vulnerabilities.
The Power of Nmap Scripting
Nmap’s core functionality lies in its ability to scan networks, gather information about hosts and services, and identify open ports. However, its true potential is unlocked through its scripting engine, enabling users to extend its capabilities beyond basic scans. Nmap scripts, written in Lua, allow for custom network interactions, enabling sophisticated security assessments and vulnerability detection.
Exploring the Scripting Landscape
Nmap’s script library, known as the NSE (Nmap Scripting Engine), offers a vast collection of pre-written scripts covering a wide range of security tasks. These scripts can be categorized into various functions, including:
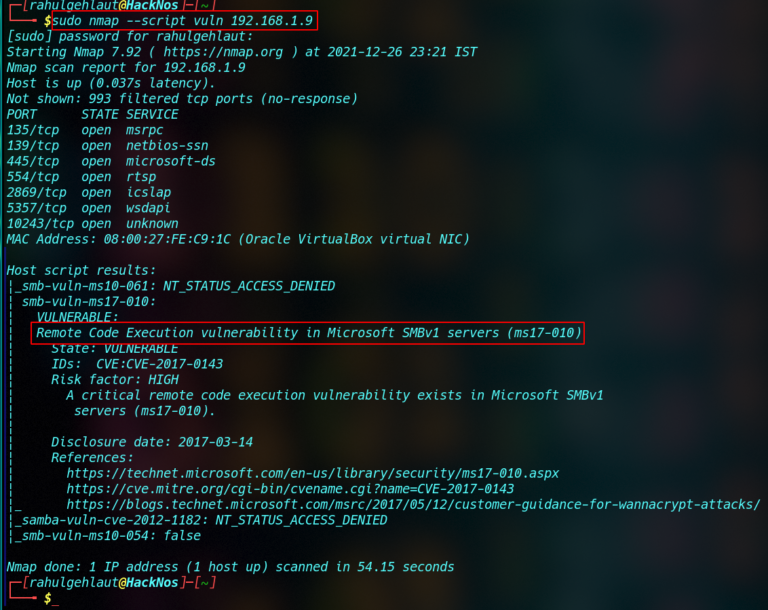
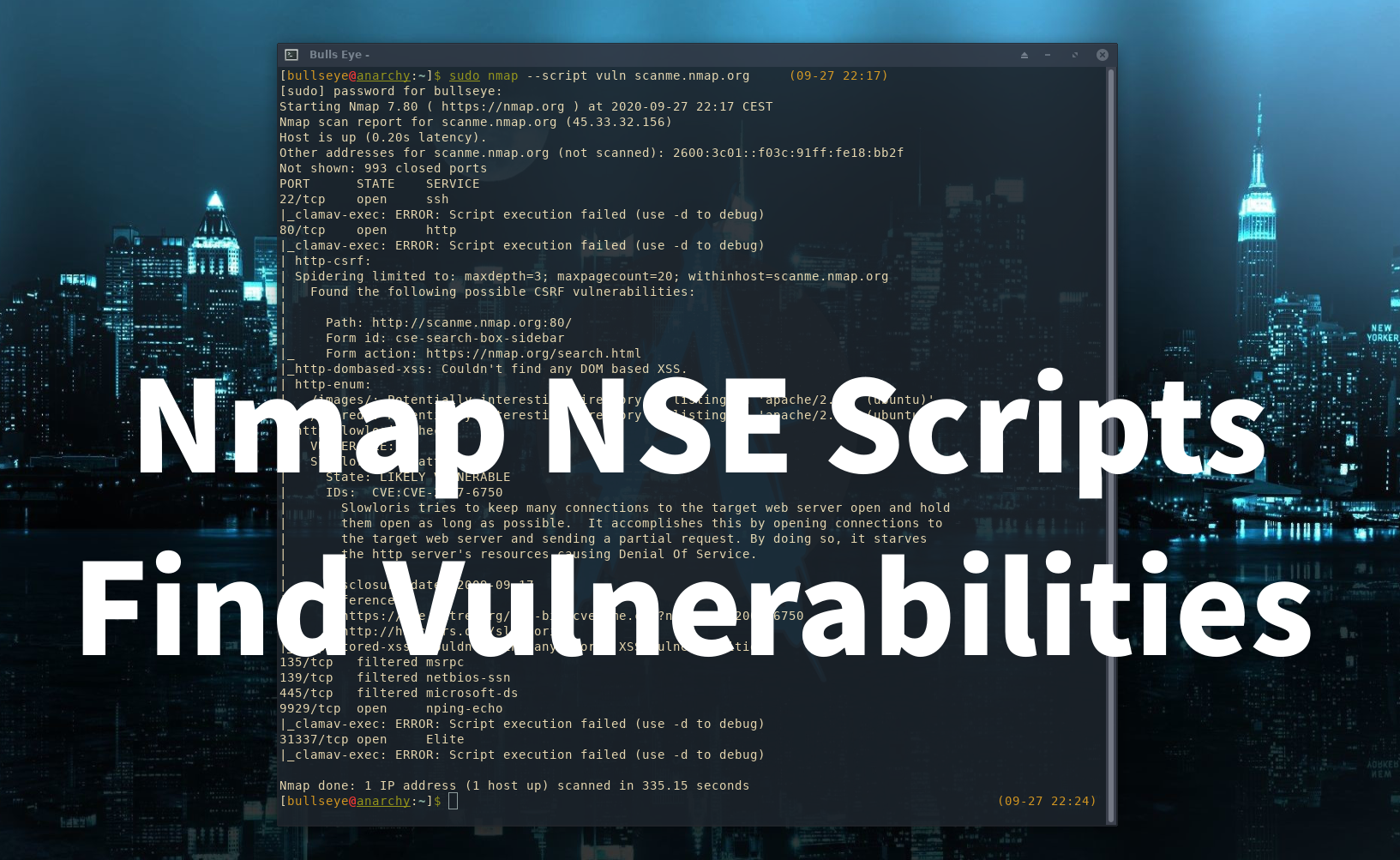
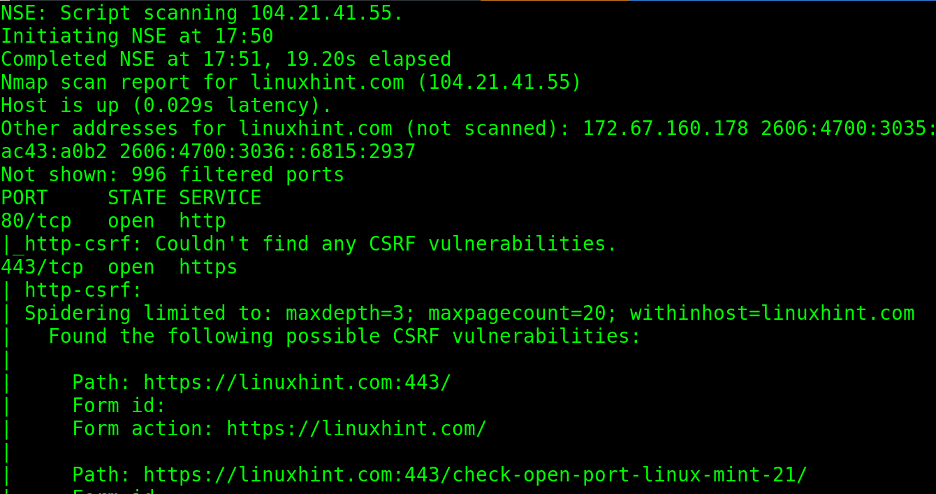
- Vulnerability Detection: These scripts identify known vulnerabilities by probing for specific configurations or behaviors indicative of security flaws. Examples include scripts detecting common web server misconfigurations, outdated software versions, or weak encryption protocols.
- Service and Protocol Analysis: These scripts analyze network services and protocols, identifying potential vulnerabilities associated with their implementation. They can probe for weaknesses in specific protocols like FTP, SSH, or SMB, revealing potential attack vectors.
- Operating System Fingerprinting: These scripts attempt to identify the operating system running on a target host based on its responses to various network requests. This information can be valuable for targeting vulnerabilities specific to certain operating systems.
- Network Discovery: These scripts aid in network reconnaissance, identifying devices, services, and open ports within a network. This information can be used for further investigation and vulnerability assessment.
Implementing Nmap Scripts: A Practical Guide
Utilizing Nmap scripts is a straightforward process. The -sC command line option allows users to run all default scripts against a target host or network. For specific scripts, the -sV option can be combined with the --script flag, followed by the script name. For instance, nmap -sV -sC --script=http-vuln-cve2010-4219 192.168.1.1 would run the http-vuln-cve2010-4219 script against the target IP address 192.168.1.1.
Leveraging Scripting for Enhanced Security Assessments
Nmap scripting provides a powerful framework for enhancing network security assessments, offering several key benefits:
- Automated Vulnerability Detection: Nmap scripts automate the process of identifying vulnerabilities, significantly reducing manual effort and time required for security analysis.
- Targeted Assessment: Scripts allow for focused analysis by targeting specific vulnerabilities or services, enabling efficient and effective vulnerability detection.
- Comprehensive Coverage: Nmap’s extensive script library provides comprehensive coverage of common vulnerabilities, ensuring thorough security assessments.
- Real-Time Analysis: Scripts can be executed in real-time, providing immediate insights into the security posture of a network or host.
- Customizability: Nmap’s scripting engine allows users to create custom scripts tailored to specific needs and environments, providing tailored vulnerability assessment capabilities.
FAQs: Addressing Common Questions
Q: How do I find the right script for my needs?
A: Nmap’s documentation provides a detailed list of available scripts, categorized by their function and target. Additionally, online resources like the Nmap wiki and forums offer guidance on script selection and usage.
Q: Can I modify existing scripts or create my own?
A: Yes, Nmap’s scripting engine is highly customizable. Users can modify existing scripts or create new ones using the Lua programming language. This flexibility allows for tailored security assessments based on specific requirements.
Q: How do I interpret the output of Nmap scripts?
A: Script output typically includes information about the vulnerability identified, its severity level, and potential remediation steps. Nmap’s documentation provides detailed explanations of script output and their interpretation.
Q: What are the limitations of Nmap scripting?
A: Nmap scripting relies on the availability of relevant scripts and their effectiveness in detecting specific vulnerabilities. Additionally, false positives and false negatives may occur, requiring further investigation to confirm actual vulnerabilities.
Tips for Effective Scripting
- Stay Updated: Regularly update Nmap and its script library to ensure access to the latest vulnerability detection capabilities.
- Understand Script Functionality: Before running a script, thoroughly understand its purpose, target, and potential output.
- Validate Findings: Manually verify any vulnerabilities identified by scripts, especially those with high severity levels.
- Prioritize Remediation: Address identified vulnerabilities promptly to mitigate potential security risks.
Conclusion
Nmap scripting empowers security professionals and network administrators with the tools to conduct comprehensive vulnerability assessments, uncovering potential security flaws and enhancing network security. By leveraging its extensive script library and customizable capabilities, Nmap scripting offers a powerful framework for proactive security analysis, facilitating early detection and remediation of vulnerabilities, ultimately safeguarding digital assets and mitigating potential threats.
![]()



Closure
Thus, we hope this article has provided valuable insights into Unveiling Network Vulnerabilities: A Comprehensive Guide to Nmap Scripting. We appreciate your attention to our article. See you in our next article!
